The site is read-only. Please transition to use Robotics Stack Exchange
| ROS Resources: Documentation | Support | Discussion Forum | Index | Service Status | ros @ Robotics Stack Exchange |
 | 1 | initial version |
Without dismissing the effort the author of wiki/ROS/Tutorials/MultipleRemoteMachines put into that tutorial, I don't believe what is described there was ever a best practice (note: it's also not that old: first edits from end of 2018).
The tutorial essentially instructs users to setup port forwarding, which exposes ROS nodes directly on the public internet. This is not a good idea.
STEP 2: Modem/Router Settings even suggests to forward all TCP and UDP ports between 1025 and 65000. Exposing all ports of a machine to the public internet.
This is also not a good idea.
It's also unnecessary.
I would strongly recommend to use a VPN or some other form of tunnel between remote networks. This has many benefits, but two main ones:
TCPROS and UDPROS traffic, which is plain text)Whether you use a commercial service or something like tinc-vpn (OSS, peer-to-peer VPN) doesn't really matter.
As to performance: anything which needs to be encrypted and decrypted will incur overhead. But that's a non-issue here I believe, as transmitting ROS messages plain text over the public internet is basically an invitation for some rogue entity to take control of your robot(s), and additionally the types of encryption employed by VPN services are typically rather lightweight.
Without getting overly dramatic: only use port-forwarding if you absolutely cannot use something else.
 | 2 | No.2 Revision |
Without dismissing the effort the author of wiki/ROS/Tutorials/MultipleRemoteMachines put into that tutorial, I don't believe what is described there was ever a best practice (note: it's also not that old: first edits from end of 2018).
The tutorial essentially instructs users to setup port forwarding, which exposes ROS nodes directly on the public internet. This is not a good idea.
STEP 2: Modem/Router Settings even suggests to forward all TCP and UDP ports between 1025 and 65000. Exposing all ports of a machine to the public internet.
This is also not a good idea.
It's also unnecessary.
I would strongly recommend to use a VPN or some other form of tunnel between remote networks. This has many benefits, but two main ones:
TCPROS and UDPROS traffic, which is plain text)Whether you use a commercial service or something like tinc-vpn (OSS, peer-to-peer VPN) doesn't really matter.
As to performance: anything which needs to be encrypted and decrypted will incur overhead. But that's a non-issue here I believe, as transmitting ROS messages plain text over the public internet is basically an invitation for some rogue entity to take control of your robot(s), and additionally the types of encryption employed by VPN services are typically rather lightweight.
Without getting overly dramatic: only use port-forwarding if you absolutely cannot use something else.
Edit: I've added a strong warning to that tutorial to dissuade people from trying to implement it (diff):
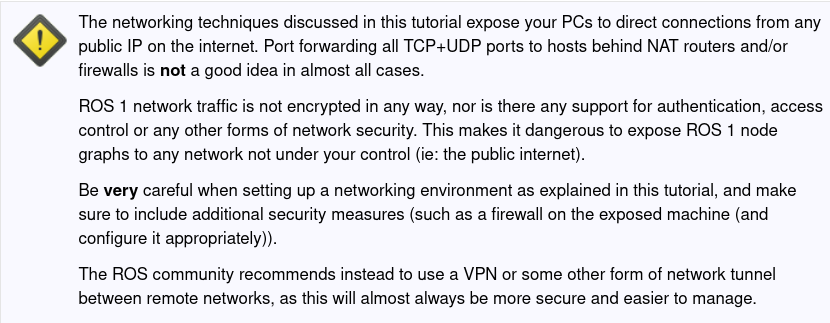
I'm actually going to discuss with some other people whether that page should be removed.
 | 3 | No.3 Revision |
Without dismissing the effort the author of wiki/ROS/Tutorials/MultipleRemoteMachines put into that tutorial, I don't believe what is described there was ever a best practice (note: it's also not that old: first edits from end of 2018).
The tutorial essentially instructs users to setup port forwarding, which exposes ROS nodes directly on the public internet. This is not a good idea.
STEP 2: Modem/Router Settings even suggests to forward all TCP and UDP ports between 1025 and 65000. Exposing just about all ports of a machine to the public internet.
This is also not a good idea.
It's also unnecessary.
I would strongly recommend to use a VPN or some other form of tunnel between remote networks. This has many benefits, but two main ones:
TCPROS and UDPROS traffic, which is plain text)Whether you use a commercial service or something like tinc-vpn (OSS, peer-to-peer VPN) doesn't really matter.
As to performance: anything which needs to be encrypted and decrypted will incur overhead. But that's a non-issue here I believe, as transmitting ROS messages plain text over the public internet is basically an invitation for some rogue entity to take control of your robot(s), and additionally the types of encryption employed by VPN services are typically rather lightweight.
Without getting overly dramatic: only use port-forwarding if you absolutely cannot use something else.
Edit: I've added a strong warning to that tutorial to dissuade people from trying to implement it (diff):

I'm actually going to discuss with some other people whether that page should be removed.
 ROS Answers is licensed under Creative Commons Attribution 3.0 Content on this site is licensed under a Creative Commons Attribution Share Alike 3.0 license.
ROS Answers is licensed under Creative Commons Attribution 3.0 Content on this site is licensed under a Creative Commons Attribution Share Alike 3.0 license.